Zero Trust Implementation
ServicesMicrosoft Solutions Partner
Get started on your path to a Zero Trust Architecture
Zero Trust is a journey, and every organization’s journey is unique. Getting started can be a daunting task, but Arctic IT can help. We’re offering a Zero Trust Architecture strategy plan and implementation services estimate, based on the Microsoft Zero Trust Roadmap, to help you on your way to a more secure future.
What’s included with the Zero Trust strategy plan and implementation estimate
PRICING: $4,995
6-8 Hour Consultation
First, we’ll host a virtual discussion to review your security posture and rate your level of risk within the six pillars of Zero Trust: Identity, Endpoints, Data, Apps, Infrastructure, and Network. On-site consultation available for an additional fee.
Strategy Plan
Next, we will perform discovery of your environment and develop a customized playbook to guide you in making improvements based on your priorities and the lowest effort for highest security reward. The playbook will consist of action items and recommendations based on the latest security best practices.
Implementation Services Estimate
Based on our findings from the consultation and strategy plan, we will build a Statement of Work (SOW) unique to your organization’s needs around Zero Trust.
From here, if you choose to work with us on the implementation services, we will discount your $4,995 investment from the total cost of the project (estimate based on the level of effort recommended).
What is Zero Trust Architecture
Zero Trust Architecture (ZTA) is defined as a security model designed to minimize lateral movement using the guiding principles of “never trust, always verify”, least privileged access, and assume breach.
Verify Identity Explicitly
Always authenticate and authorize based on all available data points, including identity, location, device health, etc.
Use Least Privileged Access
Limit user access with Just-In-Time and Just-Enough-Access (JIT/JEA), risk-based adaptive policies, and data protection to help secure data and productivity.
Assume Breach
Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to get visibility, drive threat detection, and improve defenses.
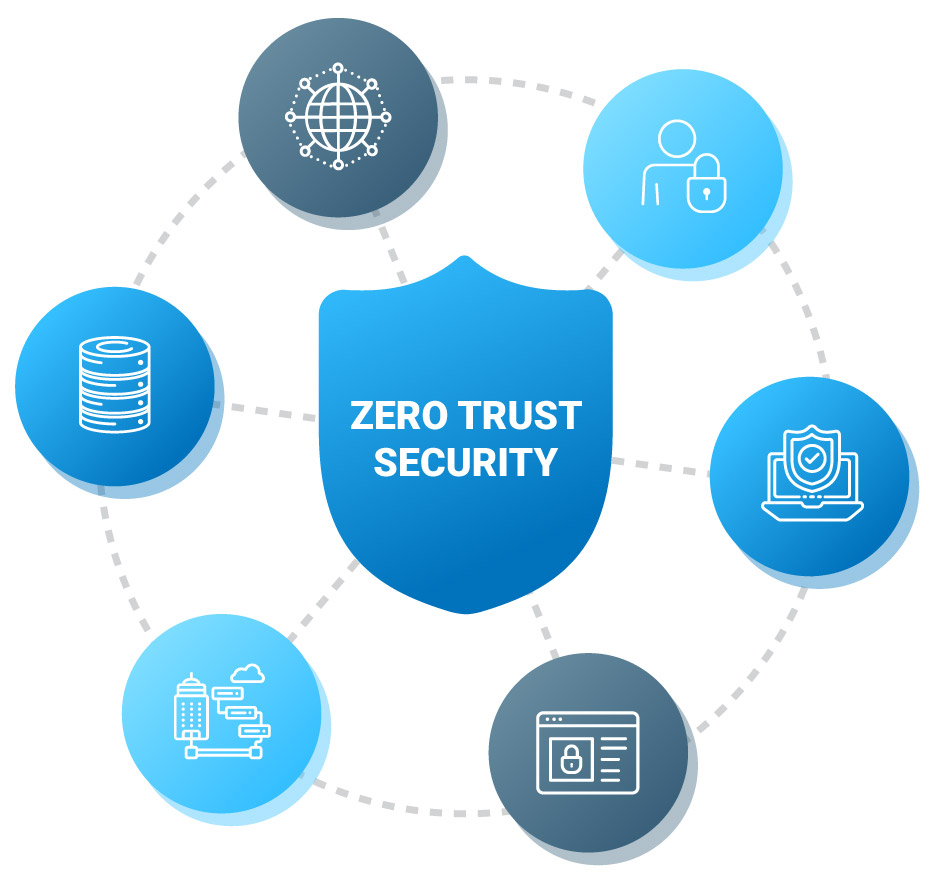
The six pillars of Zero Trust security
Identity
We’ll review how you manage identities across your organization, including multi-factor authentication and conditional access policies.
Endpoints
How do you defend your devices against cyber threats? Let’s take a look at your endpoint management, protection, and device compliance policies.
Apps
Do you practice Just in Time (JIT) Access? We’ll analyze your level of user access to applications and protections for cloud apps.
Infrastructure
How do you manage security information and events? Let’s examine your infrastructure’s defense against advanced threats.
Data
We will make recommendations based on where you are with data loss prevention, data classification, and information protection policies.
Network
Is your network segmented? How do you filter and log traffic? We’ll help make sure you are on the right track.
Benefits of Zero Trust Microsoft solutions*
%
Return on investment with a less than 6 month payback
%
Reduced risk of a data breach
%
Decrease in calls placed to IT and help desk staff
%
Reduction in management time due to improved security processes
* The Total Economic Impact™ of Zero Trust Solutions From Microsoft, December 2021. Study by Forrester Consulting, commissioned by Microsoft
Frequently asked questions about Zero Trust Architecture
Here are some of our most frequently asked questions and answers.
What type of company will benefit from Zero Trust Architecture?
Companies across various industries, especially those handling sensitive data or operating in highly regulated sectors such as finance, healthcare, and government, can benefit significantly from Zero Trust implementation. Additionally, organizations with distributed workforces, remote access requirements, or a reliance on cloud-based services can also reap the rewards of the enhanced security and data protection. In short, really any company worried about the security of their data can benefit from a Zero Trust Architecture.
Why is Zero Trust implementation important?
Traditional security models operate under the assumption that everything inside the network can be trusted. However, with the increasing sophistication of cyber threats, this approach is no longer sufficient. Zero Trust implementation ensures that security measures are applied at every level of access, reducing the likelihood of successful cyberattacks.
Can Zero Trust work with existing security measures?
Yes, Zero Trust can be integrated with existing security measures to enhance overall security posture. It complements traditional security approaches by adding additional layers of protection and reducing reliance on perimeter-based defenses.
How does Zero Trust benefit organizations?
Zero Trust implementation offers several key benefits to organizations, including improved security posture, reduced risk of data breaches, enhanced visibility and control over network traffic, better compliance with regulatory requirements, and increased resilience against evolving cyber threats. The underlying data governance model, implemented with tools like data loss prevention, provides a transition to a proactive versus reactive security posture.
How can organizations measure the effectiveness of Zero Trust?
Organizations can measure the effectiveness of Zero Trust implementation by monitoring key security metrics such as access controls, incident detection and response times, user behavior analytics, and compliance with security policies. Regular security assessments and audits can also help evaluate the overall security posture.
Will Zero Trust lock down my devices, applications, and network so they are hard to use?
Any good security solution should work with the business and not against it. While there will be change when implementing Zero Trust, it can be done as a phased approach and in a way that keeps in mind the organizations need to function at a high level while still securing your data assets from those who might look to misuse them.

Choose a Microsoft Solutions Partner
A reliable Microsoft Solutions Partner like Arctic IT can be the difference in accomplishing your technology goals. Whether it’s implementing Zero Trust Architecture or any of the other Microsoft cloud products, we have the team you need to get the job done right.
Additional Microsoft cloud implementation services
Microsoft 365 Migration
Microsoft Power Platform
End User Training
Request more information
[email protected]
