Modern cloud storage isn’t just more convenient; it’s demonstrably more secure than on-premises solutions. With built-in versioning, automated patching, and AI-powered threat detection, users dramatically reduce both the likelihood and cost of breaches.
The average data breach now costs organizations $4.88 million – a staggering 10% jump in just one year according to IBM’s 2024 Cost of a Data Breach Report. Yet, many businesses still cling to outdated security strategies, believing their on-premises file storage is the safer option. The data tells a very different story.

Why Cloud Storage Matters for Security
The dangerous myth: on-premises file storage is safer
A major misconception persists in many organizations that storing files on-premises is inherently safer than using cloud-based storage solutions. But the evidence paints a different picture.
According to the Verizon 2024 Data Breach Investigations Report, ransomware attacks frequently target legacy file shares and outdated on-prem systems, where patching is inconsistent and detection tools are lacking. In fact, ransomware was involved in 23% of all breaches, and servers (including on-prem file servers) accounted for nearly 60% of initial breach vectors.
The real-world problem: ransomware targets file shares
Ransomware groups favor on-premises file shares because they’re often unmonitored, unpatched, and lack rapid recovery options.
Organizations relying on legacy storage frequently discover too late that they don’t have recent backups, immutable snapshots, or secure offsite copies – making recovery slow and costly.
Cloud storage solutions, in contrast, benefit from:
- Proactive patching and threat detection
- Built-in redundancy and backups
- Zero-trust access controls and detailed activity logging
These layers of protection dramatically reduce the window of vulnerability compared to unmanaged on-premises file servers.
Bottom line: modernize your storage, modernize your defense
Choosing cloud storage isn’t just about convenience; it’s about eliminating one of the most common weak points in modern cybersecurity. Businesses that modernize their storage strategy are significantly better positioned to resist ransomware, data theft, and operational downtime.
Choosing the Right Cloud Storage Solution
What type of cloud storage do you need?
When migrating files to the cloud, it’s easy to ask, “Where should I put my files?” But the better question is, “How do my users and systems use those files, and what kind of cloud service matches that need?”
Your migration path will shape your storage choice. Not every cloud storage solution works the same way, and not every organization needs the same thing. Most migrations fall into one of the following three scenarios (let’s use the Microsoft Azure cloud as an example).

Scenario 1: Productivity Storage – SaaS Solutions like SharePoint or OneDrive
If your files are mostly Office documents, PDFs, images, and other team content, and you’re looking to enable collaboration and anytime, anywhere access, SaaS storage like Microsoft 365 SharePoint and OneDrive is ideal.
But migrating to SaaS often means rethinking how you organize your data. Shared drives and mapped letters disappear – replaced by SharePoint document libraries, Teams channels, and browser-based or synced access. Permissions shift from NTFS folder security to SharePoint groups and Teams membership. Power users may need training to manage files in a new interface
Productivity SaaS solutions are best for
- Creating Word, Excel, PowerPoint, and PDF files
- Collaboration and sharing
- Teams who need secure, easy file access from anywhere
Scenario 2: System Data Storage – PaaS Solutions like Azure Blob or Azure Files
If your data is primarily raw files, logs, exports, or media—and these files support other systems, ETL jobs, or analytics workflows, PaaS storage makes more sense.
These solutions don’t provide mapped drives or desktop apps. Instead, they offer scalable storage with API or file-share access, optimized for performance and automation.
Example questions to ask:
- Are these files being read and written constantly by apps or scripts?
- Are you handling large file sizes or thousands of rapid updates?
- Do your systems use SMB file shares or object storage APIs?
Data storage PaaS solutions are best for
- Machine-generated data
- ETL processes, backups, media files, and logs
- Scalable storage with fewer user-facing needs
Scenario 3: Lift-and-Shift – IaaS File Servers in Azure VMs
If your users still need mapped drives, and you’re not ready to redesign your file structure, you can run a Windows or Linux file server in Azure – giving you a familiar experience but shifting infrastructure management to the cloud.
This scenario keeps your NTFS permissions and drive letters, but you’ll still manage patching, backups, and OS updates (unless you add automation).
IaaS file servers are best for
- Legacy applications expecting network shares
- Minimal changes to user workflows
- Temporary steps before refactoring to SaaS or PaaS later
Key Insight: The type of data (and the way it’s used) should guide your cloud storage choice.
| Use Case | Cloud Model | Example |
|---|---|---|
| Office files, collaboration | SaaS | Microsoft 365 SharePoint, OneDrive |
| System files, backups, ETL workloads | PaaS | Azure Blob Storage, Azure Files |
| Legacy mapped drives, lift-and-shift | IaaS | Azure VM with Windows File Server |
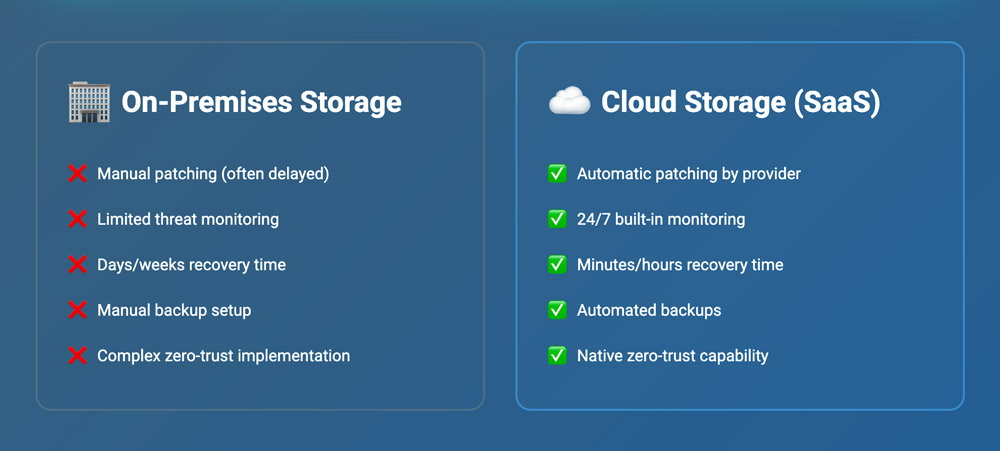
Security comparison: on-premises vs. cloud
| Factor | On-Premises | Cloud (SaaS) |
|---|---|---|
| Patching responsibility | Your team | Provider |
| 24/7 threat monitoring | Extra cost | Built-in |
| Recovery time from ransomware | Days/weeks | Minutes/hours |
| Backup automation | Manual setup | Automatic |
| Zero-trust architecture | Complex to implement | Native capability |
| AI-powered threat detection | Expensive add-on | Often included |
Backup & Versioning – Protecting Your Cloud Data
Built-in versioning: recovering productivity files quickly
In SaaS solutions like Microsoft 365 SharePoint and OneDrive, versioning is built in by default. If a user accidentally deletes, overwrites, or corrupts a document, they can quickly restore a previous version (often in seconds) without needing to call IT or restore from backup.
Cloud-based storage also makes secure sharing much easier. Instead of emailing copies of files (and creating version chaos), users can share a single source of truth through secure links with access controls, expiration dates, and permissions that are easy to adjust.
Cloud providers back up, but is it enough?
Most cloud services provide redundancy and short-term data protection out of the box. But what happens if:
- A file is maliciously deleted and you don’t notice for 90 days?
- You need to recover an entire site or shared drive from six months ago?
- A ransomware attack encrypts not just your local copies but also your synced cloud data?
That’s where dedicated backups come in.
Point-in-time vs. daily backups: What do you need?
- For productivity files, built-in version history and the Recycle Bin may be enough
- For critical business files, you may need point-in-time backups that let you restore to a precise moment before an incident
- For compliance or audit needs, longer retention (often 1–7 years) might be required
Backup responsibility changes by cloud model
| Cloud Model | Example Storage Solution | Who Manages Backup? |
|---|---|---|
| SaaS | SharePoint, OneDrive | Microsoft provides versioning & redundancy; you add cloud-to-cloud backup if needed |
| PaaS | Azure Blob, Azure Files (serverless) | You configure backups using Azure Backup or third-party solutions |
| IaaS | File server on Azure VM | You manage backups, schedules, and restore plans just like on-prem |
In short, the more control you want, the more backup responsibility you take on. SaaS keeps things simple, but PaaS and IaaS give you more flexibility (and more to maintain).
Cloud-to-cloud backup: an extra safety net for SaaS
Even with Microsoft 365’s built-in protections, many businesses add cloud-to-cloud backup solutions like Veeam, AvePoint, or Barracuda. These services provide:
- Longer retention than Microsoft’s default periods
- Simplified restore of entire sites, mailboxes, or libraries
- Protection against accidental admin actions or data retention misconfigurations
Key Insight: Cloud doesn’t mean you stop thinking about backups. It means you choose how much of that burden you want to carry yourself.
Security & Patching Responsibilities – Who Owns What?
Understanding the shared responsibility model
When moving to the cloud, one of the most important decisions you’ll make is how much control and responsibility you want over your environment. Every cloud service model has a shared responsibility between you and the provider. The more managed the service, the less you have to worry about patching and security hardening.
| Cloud Model | Example Solutions | Who Patches the App/OS? | Who Secures the Data? |
|---|---|---|---|
| SaaS | SharePoint, OneDrive, Teams | Microsoft | You |
| PaaS | Azure Blob, Azure Files (serverless) | Microsoft (platform) | You (data, config) |
| IaaS | Azure VM with File Server | You (OS, app) | You |
SaaS: simplifying security and reducing guesswork
In SaaS solutions like Microsoft 365, much of the guesswork, application, and verification of patches, updates, and security hardening is removed from your team’s daily responsibilities. Microsoft handles:
- OS patching
- Service-level security (encryption, network access, platform vulnerabilities)
- Built-in compliance with major frameworks like SOC 2, ISO 27001, and FedRAMP
This frees your team to focus on setting up proper permissions and sharing policies, auditing access and training users on secure collaboration.
PaaS and IaaS: more control, more responsibility
If you choose PaaS storage (Azure Blob, Azure Files), Microsoft still secures the underlying infrastructure, but your team must:
- Configure access controls (role-based access, shared access keys)
- Set up firewalls, private endpoints, and encryption policies
- Ensure backups and monitoring are configured correctly
If you choose IaaS, much of the responsibility shifts back to your team, though it’s still less than fully managing on-prem hardware:
- You’ll patch the OS (Windows or Linux)
- Manage your antivirus, backup agents, and network configuration
- Harden the VM against vulnerabilities
The less control you keep, the less risk your team carries because Microsoft takes on those security and patching tasks. The more control you want, the more processes your internal teams must maintain
Key Insight: Understanding how much risk your organization is willing to manage directly should guide your choice between SaaS, PaaS, and IaaS.
Authentication & Identity – Who Should Access Your Cloud Storage, and How?
Modern authentication brings modern security
Choosing the right cloud storage model isn’t just about where your files live; it’s also about who can access them and how you protect that access.
Modern identity solutions like Microsoft Entra ID (formerly Azure Active Directory) bring powerful features that traditional Active Directory alone can’t provide, such as:
- Conditional Access – control access based on location, device compliance, user risk, or app sensitivity
- Multi-Factor Authentication (MFA) – ensure that stolen passwords alone aren’t enough to break in
- Phishing-resistant authentication – through passwordless options like FIDO2 security keys or device-based sign-ins
- Single Sign-On (SSO) across Microsoft 365 and thousands of third-party SaaS apps
When you still need on-prem Active Directory
For organizations with significant on-premises infrastructure, a hybrid model makes sense. You can sync your on-prem Active Directory with Entra ID using Entra Connect, allowing users to:
- Sign in with their existing usernames and passwords
- Seamlessly access both cloud and on-prem resources
- Gradually move toward cloud-native authentication as legacy systems retire
This approach lets you protect your cloud storage with modern security features while maintaining compatibility with on-prem file servers, legacy applications, or domain-joined PCs.
Aligning identity with your cloud storage model
| Cloud Model | Identity Recommendation | Key Security Features |
|---|---|---|
| SaaS | Entra ID (Azure AD) + Conditional Access, MFA | SSO, automated provisioning, risk-based controls |
| PaaS | Entra ID or service principals for automation | Role-based access, secure keys, private endpoints |
| IaaS | Hybrid (Entra ID + Active Directory) | Group policies, NTFS permissions, VPN or private networking |
Key Insight: Modern authentication isn’t just about making logins easier; it’s about reducing risk through smart policies, strong authentication factors, and limiting attack surfaces.
Addressing the Root Cause of File Storage Breaches
Why do breaches still happen?
Despite growing awareness of cyber threats, file storage breaches continue to be one of the easiest points of entry for attackers. The causes are often basic security gaps that are preventable with the right cloud approach.
Here are some of the top causes of on-premises file storage breaches:
- Poor Patching: Many file servers and supporting systems go unpatched for months, leaving them exposed to known vulnerabilities.
- Phishing + Poor Authentication: Attackers increasingly use AI-powered phishing campaigns to steal user credentials, gaining initial access to corporate networks. 68% of breaches involve a non-malicious human element.
- Weak Backup Strategy: Even when backups exist, attackers often sit quietly in a network for weeks or months, corrupting backups or ensuring malware spreads before launching a ransomware attack.
- Flat Network Design: On-prem environments often lack segmentation, so an attacker who breaches one file share can easily pivot to others.
Why cloud-native storage reduces these risks
Cloud platforms like Microsoft 365 and Azure operate on a zero trust model and automate many of the defenses that on-premises systems leave as manual tasks. For example:
- Microsoft applies patches and monitors threats 24/7, globally
- Cloud storage integrates with modern authentication, blocking stolen credentials with Conditional Access and MFA
- Versioning and immutable backups in cloud storage prevent attackers from wiping out your last clean copy
- Cloud-native audit logs and anomaly detection surface suspicious behavior faster
In contrast, many on-prem file environments lack:
- Up-to-date antivirus and threat detection
- Centralized logging and alerting
- Immutable, offsite backups
- Regular testing of restore processes
This makes them a prime target for ransomware groups who rely on businesses having no viable recovery path. Breaches involving stolen credentials took an average of 292 days to identify and contain – the longest of any attack vector.
Key Insight: Cybersecurity isn’t just about preventing attacks; it’s about ensuring your recovery plan works even when attackers try to sabotage it. Cloud-native storage gives you recovery options that ransomware gangs can’t easily destroy.
Recommendations for Migrating to Cloud Storage
Start with a full migration, not a temporary fix
For most organizations, the right first step is to rethink how you store and manage your files, not just move your legacy file shares to the cloud. A full migration to a modern cloud storage solution (such as SharePoint, OneDrive, and Azure Files) creates a clean break from legacy risks.
Why a full migration?
- It forces you to evaluate your data structure and break away from flat, messy shared drives
- You eliminate old permissions and outdated files that no longer need to be migrated
- You move to a platform built for modern collaboration, versioning, and sharing
- It simplifies management going forward with no more legacy servers to patch or maintain
While a hybrid approach (keeping some file shares on-prem) may be a short-term bridge, the goal should be a fully cloud-based storage model. Hybrid environments often:
- Prolong complexity and duplicate management efforts
- Keep your organization tied to old security risks
- Delay realizing the full benefits of cloud collaboration and mobility
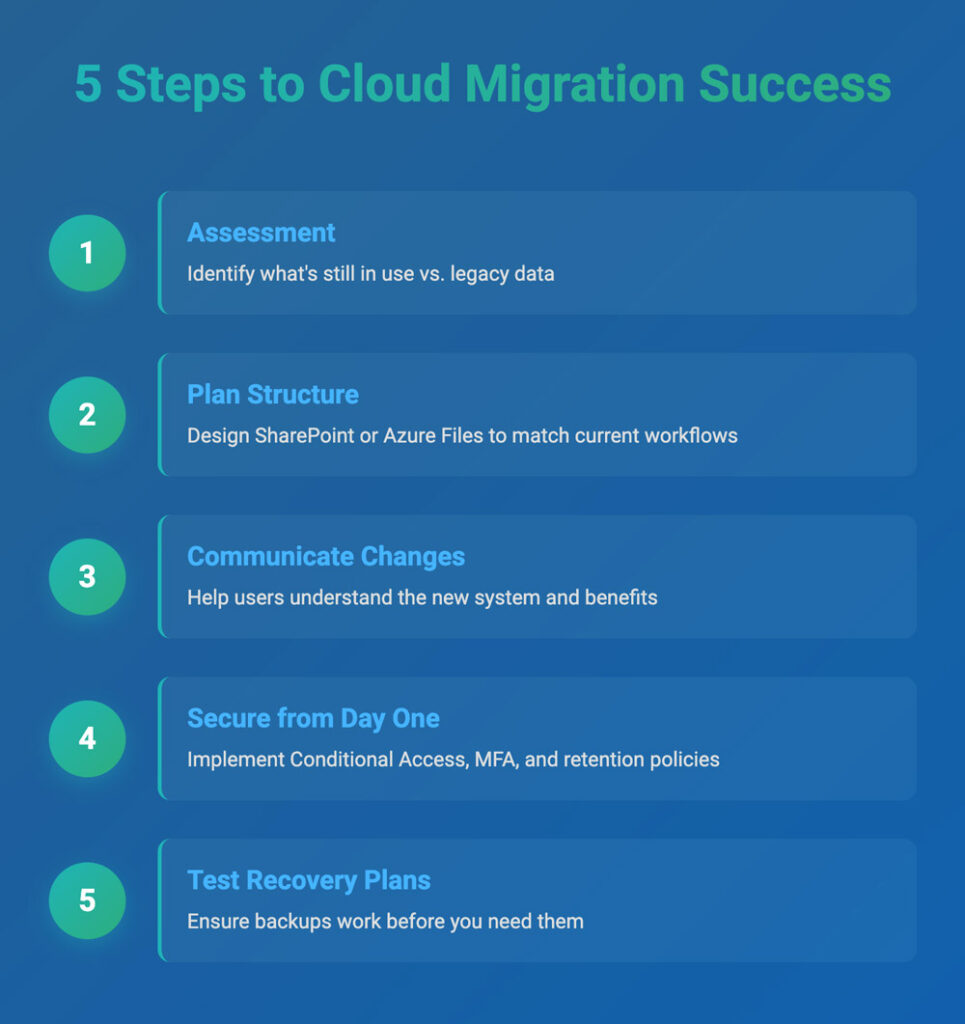
5 best practices for a cloud storage migration
- Start with an assessment. Identify what’s still in use vs. what’s legacy
- Plan your SharePoint or Azure Files structure to align with how your teams work today, not how they worked a decade ago
- Communicate the changes – help users understand how to access files in the new system and why mapped drives are being replaced with SharePoint libraries or Teams channels
- Secure the environment from day one with Conditional Access, MFA, and retention policies
- Test your backups and recovery plans to ensure you’re ready for the unexpected
How Arctic IT can help
At Arctic IT, we help organizations design and execute end-to-end cloud storage migrations that don’t just move your data, they transform how your business works. Whether you’re starting with a pilot or ready for a full migration, we build a roadmap aligned to your goals. Connect with us today to get started on your cloud storage journey.
The best time to rethink your file storage is before the next crisis forces you to. Cloud storage is not just safer – it’s a better way to work.
By Phillip Jackson, Chief Information Officer at Arctic IT

