With an unprecedented escalation in cybercriminal activity through the past year showing no signs of slowing, it has never been more critical to review your organization’s security posture. Cybersecurity regulations are expanding and impacting all industries, which can make compliance a daunting task. Organizations who have taken action to increase their cybersecurity measures may be finding that the restrictions in accessibility have taken a toll on their teams’ productivity.
Government agencies and contractors have especially felt this impact. In response to the shift towards more robust security and compliance, many choose to move their infrastructure to the Microsoft Government Community Cloud (GCC). The GCC offers a version of Microsoft 365 business applications and adds “next level” security components explicitly built for U.S. federal, state, local, tribal, and territorial government entities and organizations that work closely with the U.S. government to meet strict compliance and cybersecurity requirements.
Microsoft built the Government Cloud with unique security controls available, enabling government agencies and certified IT partners to create policies for government tenants that achieve an equilibrium between security and accessibility. You get the best of both worlds – maintain usage of the Office 365 apps you love while taking advantage of security and compliance the GCC offers.
Security and compliance policies available in Microsoft 365 GCC
If you subscribe to a Microsoft 365 GCC Plan (G3 or G5), various security controls within the Microsoft 365 Security & Compliance Center allow global admins to set and monitor compliance policies for your organization. A few notable policies and services you can implement today to enhance your security posture include:
Data Loss Prevention Controls
To prevent leaks of sensitive information, you can implement Data Loss Prevention (DLP) to protect all the types of data your agency handles, including Personally Identifiable Information (PII). These policies are implemented to monitor PII, incident reports, and other protected data on platforms like Teams chats and Outlook emails. Alerts are generated when protected data is detected in communication flows.
Extended Device Controls
In the world of BYOD, where employees expect the convenience and flexibility to work from anywhere, on their chosen device, and have access to data anytime in a timely fashion, organizations are presented with a unique challenge to offer this flexibility while maintaining required data security. Thanks to Microsoft Mobile Application Management (MAM) policies, organizations have a mechanism to create safe segregated “workspaces” on employees’ mobile devices that separate company data from their personal data. MAM allows organizations to maintain data security while allowing the employees to remain productive, where technology and security do not get in the way of the employees.
Policies can be added to extend DLP requirements by limiting functions such as copying protected data from company documents to personal devices and saving company data to other unsanctioned third-party cloud storage services like Dropbox, iCloud, etc. Other examples include restricting the printing of company data from mobile devices or preventing the copying of company data from work documents to personal spaces like Apple Notes/Google Keep, etc.
Device Management and Configuration Policies
Device Management Policies can also be used to control and protect company data on personal devices (e.g., government employees accessing email or Word documents on their mobile devices), further enabling secure work on the go.
Configuration profiles can be deployed to enforce secure configurations and security controls for all your organization’s Windows and Mobile (Android and iOS) devices. Compliance policies evaluate each device to see if it meets the required health posture. If the device is not compliant with an outdated version or missing required patches, it can be blocked from access until the deficiencies are addressed. Also, if the device storage is not encrypted, access to agency resources from the device is restricted to avoid exposure of company data to unprotected storage.
Continuous Device Security
Device management services are available to ensure required security settings are maintained throughout a device’s lifecycle, keeping it compliant with standards. Suppose the device’s antivirus gets temporarily turned off during a routine process like an update. In that case, security policies can be established to ensure protections are turned back on after completing the tasks to maintain your endpoint’s security posture.
Grace Period
Agency devices can be consistently monitored to provide notification if there are security or health issues. When a problem is identified, an alert is sent to both the employee and the administrator. A grace period can be implemented to place a hold on rejecting the device for an allotted amount of time, allowing the employee to stay productive until the issue can be resolved.
Conditional Access Policies
Gone are the days of ‘one size fits all’ when it comes to security. Organizations today may encounter unique security requirements calling for custom security controls. Conditional Access (CA) Policies in the Microsoft cloud allow an organization to define granular access control policies for their cloud resources. CA policies provide a risk-based approach to managing data security versus traditional static policies that may no longer fit unique situations or hinder staff performance by overreaching. Organizations have the power to respond to requirements like access restrictions from specific geographic locations, requiring extra authentication for high-security data or cloud apps, allowing only a particular group of staff access to a specialized cloud application, among other special needs.
Identity Security Services
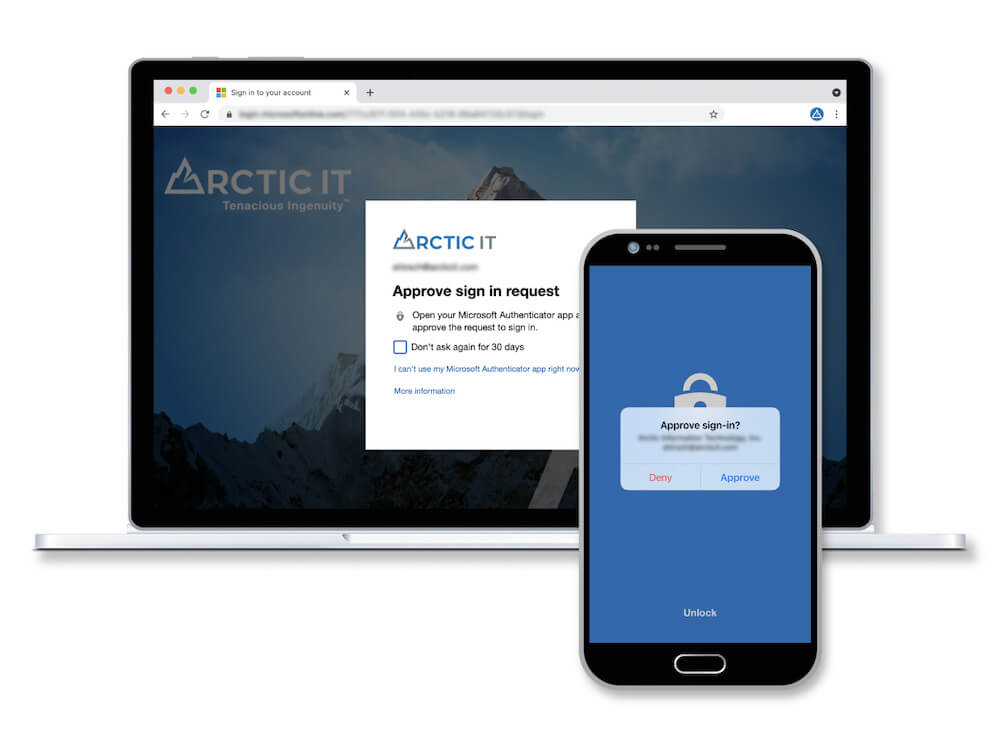
With the rise of cyber-crime and system breaches, it is evident that passwords alone no longer provide sufficient security to match current and emerging threats. Increase confidence that only authorized members of your team have access to your information resources by enabling identity security services in Azure Active Directory. Multi-Factor Authentication (MFA) is an authentication service that adds a layer of security when accessing your cloud resources and helps prevent 99.9 percent of attacks on your Microsoft accounts. By activating MFA, your organization is protected from attacks such as password spray and credential stuffing.
Another identity security service, Privileged Identity Management (PIM), allows you to control and monitor access to sensitive resources across your organization. With PIM, you can see reports on how long a user has had admin access and when they operated using this privilege. You can also use PIM to protect your Global Administrator position and offer approval-based role activation to minimize the risk of access permissions abuse.
Microsoft Defender for Endpoint
More than an antivirus, the Microsoft Defender for Endpoint service provides IT Threat and Vulnerability Management for your organization’s devices. It will continually check for vulnerabilities to ensure everything is updated, highlight what is missing, and help prioritize remediation efforts.
Today, the number of logs generated by security systems like this can quickly become overwhelming. Organizations are left at risk of missing critical events or lack visibility into what signals may be related and are part of an attack chain in an environment. The Microsoft Defender security engine has the intelligence to correlate events and automatically remediate certain threats before you may even know anything is amiss, greatly reducing the Mean Time to Respond (MTTR).
Getting started with Microsoft 365 for Government
As outlined above, the Microsoft 365 GCC can help you achieve a more protected environment while allowing your team to operate more productively as a secure mobile workforce. You get the best-in-class office apps you’re already using combined with the tools you need to maintain compliance.
Arctic IT can partner with you to implement the security and compliance policies that matter most to your organization, if you don’t know where to begin. We are a certified reseller of GCC licensing, a Microsoft Gold Partner, and experienced in helping government agencies thrive in the Microsoft cloud. Connect with us today at [email protected] to learn more.

By Kuda Mazorodze, Security Operations Manager at Arctic IT

